Cisco Threat Response – Security that works Together
– “Pulkit Mittal – Network and Security Engineer”
The work of a Security Analyst can be time-consuming. It requires hours of manual investigation, detection and remediation. I have spent hours day and night working across threats, moving from one endpoint to another to detect the source component by putting the pieces together.
The time spent on a single threat changed my focus to use a more robust approach for our IT Security Operations. The time taken to triage and investigate a threat significantly reduced from hours to minutes after the adoption of the Cisco Threat Response.
Since the first release of this platform, it has been providing an incredible amount of information needed to activate the alerts and this has continuously improved over the year. With no doubt, I can say that our security team is much more confident about our operations. The most awarding part for our existing customers is that Cisco Threat Response as a platform comes at no cost! It comes with the license for any Cisco Security product that it has integrations. This ensures that any investment in any Cisco Security product made by the customers will provide them with the best professional services so that they feel safe running their business.
CTR in Action
Recently, we came across an executable that was spreading across the network hopping from one network to another and trying to reach the servers. With the Cisco Threat Response, we were able to locate the malicious program analyzed by our Threat Grid Malware Analysis and take action by blocking the malicious hash from the same within no time.
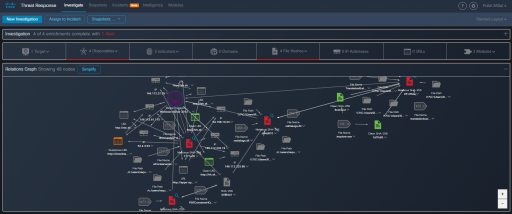
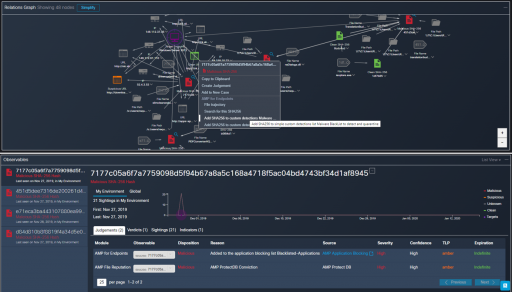
The Relation Graph provides an intuitive, interactive visualization for better situational awareness of the network and endpoints marking the malicious and clean points in the networks. The grey areas are investigated further by our experienced security team to ensure that the entire network is secure from any potential malware.

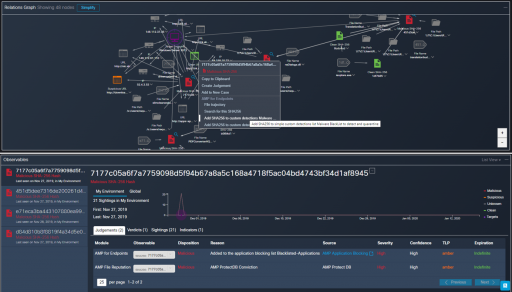
The integration with the malware detection and endpoint security Cisco tool “AMP for Endpoints” enabled our team to block the malicious SHA in the environment using one of the numerous capabilities of the CTR platform.
Benefits
Cisco Threat Response provides value by unleashing the full power of an integrated security architecture.
- Out-of-box integrations – Provides management flexibility and a holistic view of the network using your existing Security investments.
- Save time and effort – Speeds up cyber investigations by taking corrective action immediately.
- No additional cost – Easily integrates with existing Security product licenses and comes at no additional cost with any new investments made.
Evolution
The power of this platform is an endgame to the old cybersecurity methodologies and practices. We are able to run our SOC operations much faster with expertise across the Cisco Security products and management via the Cisco Threat Response. We love this Cisco release and excited about what we have on the roadmap.
To get these best features, benefits and management of your network, register for a free trial of any of our Cisco Security product offerings at Kytec Security Solutions.